IAM Best Practices
Implementing
Identity and Access Management (IAM) effectively is the difference
between a secure environment and a wide-open door. In 2026, the strategy has
shifted from "perimeter security" to "identity-first
security."
Here is a
breakdown of the current best practices for managing identities.
1. Core
Principles
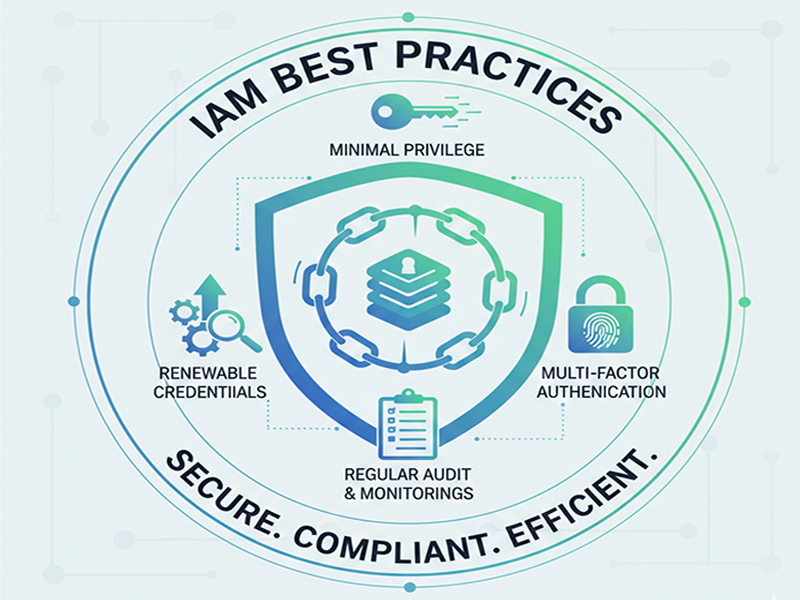
- Principle of Least Privilege
(PoLP): Grant
only the minimum permissions required for a task. Instead of broad
"Admin" or "Editor" roles, use granular permissions
(e.g., Storage Object Viewer).
- Zero Trust Architecture: Assume no user or device is
trustworthy by default, even if they are on the internal network. "Never
trust, always verify."
- Separation of Duties: Ensure that no single person
has enough permissions to complete a high-risk process (e.g., the person
who requests a payment shouldn't be the one to approve it).
2.
Authentication & Access
- Universal MFA: Enforce Multi-Factor
Authentication for every user.
- Pro Tip: Shift toward phishing-resistant
MFA like FIDO2/WebAuthn (hardware keys) rather than SMS or email
codes.
- Single Sign-On (SSO): Centralize authentication to a
single provider (like Okta, Entra ID, or Google Cloud). This reduces
"password fatigue" and ensures that when an employee leaves, you
only have one door to lock.
- Just-in-Time (JIT) Access: Don’t give permanent
"standing" privileges. Use tools that grant elevated access only
for the duration of a specific task.
3.
Managing Non-Human Identities
In 2026,
service accounts and AI agents often outnumber human users.
- No Hardcoded Secrets: Never store API keys or
passwords in code. Use a Secrets Manager (e.g., AWS Secrets
Manager, HashiCorp Vault).
- Workload Identity: Use short-lived, token-based
authentication for applications and containers rather than long-lived
secret keys.
- Identify "Orphaned"
Accounts:
Regularly scan for service accounts that are no longer tied to an active
application and disable them.